Introduction:
I guess that you may have heard of HIDDEN Essids, or may be have seen it while scanning for WIFI with your mobile, computers etc.
So, what is Hidden ESSID?
Its nothing but a way of securing your wireless by making it invisible to other people by not broadcasting the ESSID. Only people who know the ESSID can search for it and connect to it.But is it really secure?? I tell you its insecure than having a Visible ESSID. Why??
Because if you have a broadcasted ESSID you will be very careful on choosing password that wont match your ESSID. But when its hidden, you will think of yourself as secure and may not put the password at all, or may just put a weak password (matching essid itself)...But its just a possiblity, there is no need for a hidden ESSID to have same password too LOL!!
After boring introduction, lets get to the main point:
Principle:
Its really simple to crack the hidden Essid. The method we are going to do now works on the principle that when an authorized machine connects to the Hidden ESSID while we are sniffing / capturing data from wireless, then we can capture the ESSID from the authentication packets.
**apart from this method there are options of bruteforcing and dictionary attack which are usually not even needed.
Proof:
Test AP Essid: DeathKnight
Test AP BSSID: 00:19:5B:4C:FA:5B
Tools used: Airodump-ng and aireplay-ng from aircrack-ng suite.
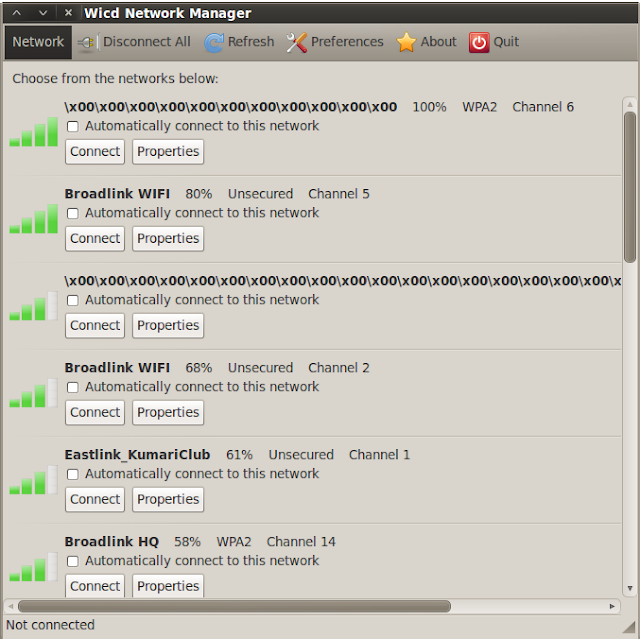
First we scan for wireless using wireless manager. I am using wicd as it is preinstalled in BackTrack R1.
The first one is my test network. It is shown as \x00\x00 because of some bug in WICD network manager, which I cant fix. It should have been shown as <hidden>. :D
Lets check the properties of this network to get more informations:
Here, its WPA2 encrypted, is in channel 6 and its BSSID is 00:19:5B:4C:FA:5B.
Now, lets capture the packets for this Network from this information.
I will use airodump-ng to capture it, you may use other too.
airodump-ng -c 6 --bssid 00:19:5B:4C:FA:5B mon0
Ok, the information we got is, it has Essid of length 12 and there is a client with BSSID 30:38:55:05:49:45 connected, which is my nokia e72. Keep this running, open a new tab and follow next instruction.
Now, since a client is already connected we dont have to wait for another client to connect to the network, we can just kick him out using "aireplay-ng" because of which he will be automatically reconnected or may manually reconnect to.
aireplay-ng -0 5 -a 00:19:5B:4C:FA:5B -c 30:38:55:05:49:45 mon0
This command will send 5 deauthentication packets to the client.
Now lets check our airodump-ng tab.
Hurrah!! The ESSID has been revealed while the client was reconnecting back, and if you look at the righ-top of the picture you can see
[ WPA handshake: 00:19:5B:4C:FA:5B
which can be used to crack the WPA2 key of the network too. So it is two birds in one shot.
Finally, lets once again check our Wireless Manager WICD.
You can see the network DeathKnight WPA2 Channel 6, which was our target network.
Conclusion: Only Hidden ESSID is not a good means of security, in fact it isnt even a means of security as ESSIDs were never meant to be hidden as I have read in some articles.
This tutorial takes just about 3-5 minutes. :)
I guess that you may have heard of HIDDEN Essids, or may be have seen it while scanning for WIFI with your mobile, computers etc.
So, what is Hidden ESSID?
Its nothing but a way of securing your wireless by making it invisible to other people by not broadcasting the ESSID. Only people who know the ESSID can search for it and connect to it.But is it really secure?? I tell you its insecure than having a Visible ESSID. Why??
Because if you have a broadcasted ESSID you will be very careful on choosing password that wont match your ESSID. But when its hidden, you will think of yourself as secure and may not put the password at all, or may just put a weak password (matching essid itself)...But its just a possiblity, there is no need for a hidden ESSID to have same password too LOL!!
After boring introduction, lets get to the main point:
Principle:
Its really simple to crack the hidden Essid. The method we are going to do now works on the principle that when an authorized machine connects to the Hidden ESSID while we are sniffing / capturing data from wireless, then we can capture the ESSID from the authentication packets.
**apart from this method there are options of bruteforcing and dictionary attack which are usually not even needed.
Proof:
Test AP Essid: DeathKnight
Test AP BSSID: 00:19:5B:4C:FA:5B
Tools used: Airodump-ng and aireplay-ng from aircrack-ng suite.
First we scan for wireless using wireless manager. I am using wicd as it is preinstalled in BackTrack R1.
The first one is my test network. It is shown as \x00\x00 because of some bug in WICD network manager, which I cant fix. It should have been shown as <hidden>. :D
Lets check the properties of this network to get more informations:
Here, its WPA2 encrypted, is in channel 6 and its BSSID is 00:19:5B:4C:FA:5B.
Now, lets capture the packets for this Network from this information.
I will use airodump-ng to capture it, you may use other too.
airodump-ng -c 6 --bssid 00:19:5B:4C:FA:5B mon0
Ok, the information we got is, it has Essid of length 12 and there is a client with BSSID 30:38:55:05:49:45 connected, which is my nokia e72. Keep this running, open a new tab and follow next instruction.
Now, since a client is already connected we dont have to wait for another client to connect to the network, we can just kick him out using "aireplay-ng" because of which he will be automatically reconnected or may manually reconnect to.
aireplay-ng -0 5 -a 00:19:5B:4C:FA:5B -c 30:38:55:05:49:45 mon0
This command will send 5 deauthentication packets to the client.
Now lets check our airodump-ng tab.
Hurrah!! The ESSID has been revealed while the client was reconnecting back, and if you look at the righ-top of the picture you can see
[ WPA handshake: 00:19:5B:4C:FA:5B
which can be used to crack the WPA2 key of the network too. So it is two birds in one shot.
Finally, lets once again check our Wireless Manager WICD.
You can see the network DeathKnight WPA2 Channel 6, which was our target network.
Conclusion: Only Hidden ESSID is not a good means of security, in fact it isnt even a means of security as ESSIDs were never meant to be hidden as I have read in some articles.
This tutorial takes just about 3-5 minutes. :)







No comments:
Post a Comment