contd...
If you havent read part (I) of this tutorial then please do, its here.
Warning: If misused this really really will cause a havoc, and I am not joking. You should only use this on the network you are authorized to fiddle with. :P
In this session, my network interface is wlan0, my MAC-address is 12:23:34:45:56:78, my test AP: DeathKnight (WPA2-PSK Encrypted) , test AP MAC-address 00:16:01:ED:2B:CB
First get your wireless card in monitor-mode.
airmon-ng start wlan0
You will get a new interface mon0.
1) Beacon Flood Mode:
Now, if you remeber previous post, "b" was the first option. Try "mdk3 --fullhelp", You will see that "b" is for "beacon flood mode". With correct options, what it does is, it floods the area with random or given ESSIDs so that when you scan with your wifi enabled device you will see tons of Wireless Networks around you. This one is not harmful. :D
The options in "beacon flood mode" are:
Ok, the basic beacon flood command is just:
mdk3 mon0 b
Try it and scan with your wifi device like mobile or another pc or anything, you will see large number of essids, now to play with the options to make it more interesting.
*if -n is not specified it sends out random ESSIDs like:
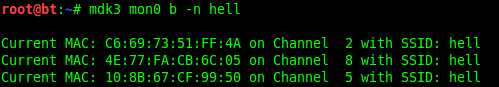
*with -n <essid> specified it sends the ESSID of our desire:
* for -f, we first need to create a text file with lots of essids of our choice, you can put anything you want :D. The output will be like this:
* -d will show the station as ad-hoc when scanned with wifi devices.
here, "hell" is the essid from mdk3, and in Mode, you can see that it is Ad-Hoc
* -w will show our spam essid as wep encrypted, just add -w, no need to assign key.
* -g will show our station as 54 Mbit. nothing special here.
* -t and -a will show our AP as WPA encrypted, TKIP and AES respectively.
* I did not find any visible effect of -h and -m option.
* -c option will allow you to fix the channel for your Spam AP. eg:
mdk3 mon0 -n hell -c 12 -w
it will flood essid called hell in channel 12 with WEP encryption.
* -s just set the speed for packets, nothing importan here.
Some of the combinations:
mdk3 mon0 -f filename -c 11 -a
essids from selected file will be flooded in channel 11 with AES encryption
mdk3 mon0 -w
will flood environment with randomley generated essid with wep encryption.
Try out some of the combinations. Your neighbour may be happy too see lots of unsecured WIFI network in the area. But if he sees something like this
This "beacon flood mode" is more fun to use with deauthentication mode, which we will discuss in next tutorial. :)
If you havent read part (I) of this tutorial then please do, its here.
Warning: If misused this really really will cause a havoc, and I am not joking. You should only use this on the network you are authorized to fiddle with. :P
In this session, my network interface is wlan0, my MAC-address is 12:23:34:45:56:78, my test AP: DeathKnight (WPA2-PSK Encrypted) , test AP MAC-address 00:16:01:ED:2B:CB
First get your wireless card in monitor-mode.
airmon-ng start wlan0
You will get a new interface mon0.
1) Beacon Flood Mode:
Now, if you remeber previous post, "b" was the first option. Try "mdk3 --fullhelp", You will see that "b" is for "beacon flood mode". With correct options, what it does is, it floods the area with random or given ESSIDs so that when you scan with your wifi enabled device you will see tons of Wireless Networks around you. This one is not harmful. :D
The options in "beacon flood mode" are:
Ok, the basic beacon flood command is just:
mdk3 mon0 b
Try it and scan with your wifi device like mobile or another pc or anything, you will see large number of essids, now to play with the options to make it more interesting.
*if -n is not specified it sends out random ESSIDs like:
*with -n <essid> specified it sends the ESSID of our desire:
* for -f, we first need to create a text file with lots of essids of our choice, you can put anything you want :D. The output will be like this:
* -d will show the station as ad-hoc when scanned with wifi devices.
here, "hell" is the essid from mdk3, and in Mode, you can see that it is Ad-Hoc
* -w will show our spam essid as wep encrypted, just add -w, no need to assign key.
* -g will show our station as 54 Mbit. nothing special here.
* -t and -a will show our AP as WPA encrypted, TKIP and AES respectively.
* I did not find any visible effect of -h and -m option.
* -c option will allow you to fix the channel for your Spam AP. eg:
mdk3 mon0 -n hell -c 12 -w
it will flood essid called hell in channel 12 with WEP encryption.
* -s just set the speed for packets, nothing importan here.
Some of the combinations:
mdk3 mon0 -f filename -c 11 -a
essids from selected file will be flooded in channel 11 with AES encryption
mdk3 mon0 -w
will flood environment with randomley generated essid with wep encryption.
Try out some of the combinations. Your neighbour may be happy too see lots of unsecured WIFI network in the area. But if he sees something like this
This "beacon flood mode" is more fun to use with deauthentication mode, which we will discuss in next tutorial. :)





Nice tutorial! Waiting for the next one...
ReplyDeletethanks. keep checking. I am not having much free time now, so i posted as much as possible on the same day last time. keep checking, I am thinking of writing a small metasploit or SET tutorial.
ReplyDeletestill.. i dont want to post much illegal/blackhat stuffs here.. so i am not sure if i want to write a metasploit tutorial in details or not.. :(
ReplyDeleteYou can write but not be very verbose. Just give directions and leave the readers to explore. I think it's the best way to learn.
ReplyDeleteok. a simple metasploit tutorial+article that explains what it does.... but not as detailed as spoonfeeding. :)
ReplyDeletei tried it but is does not work on backtrack 5
ReplyDeleteroot@bt:~# mdk3 mon0 b
Interface mon0:
ioctl(SIOCGIFINDEX) failed: No such device
Brother, you have not enabled monitor mode. Please enable it first before using mdk3.
Deleteairmon-ng start yourinterfacename.